Ubuntu 22.04 docker image is broken. Why not to use :latest in your images?
They say it’s always a good idea to pin your dependency versions to specific versions and not use things like “:latest” as base docker image or just a major version in your Python’s requirements.txt.
But why is that exactly? And what happens if you don’t do it?
If you have a Python project, this seems a pretty harmless definition in your requirements.txt:
django==4.0.3
Not only harmless, it even looks like a bright idea. After all, your going to get all minor releases with bug fixes from the Django 4.* release line.
Yeah, until that project introduces breakable changes. Most of the type that is not intentional, but still will break your build and maybe even your customer deployments, depending how you deploy.
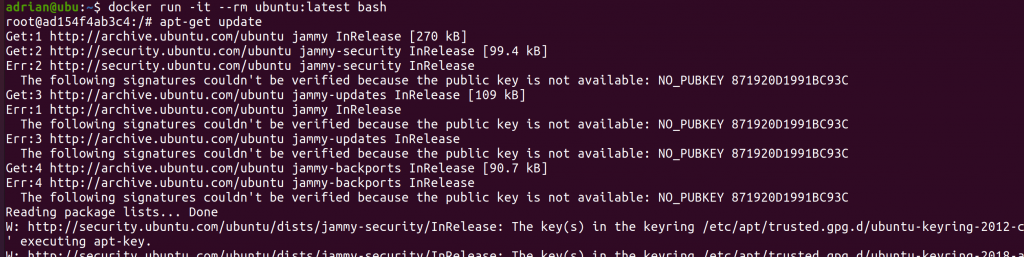
For instance at this very moment, if you have a docker image definition that derives from ubuntu:latest your image won’t work:
docker run -it --rm ubuntu:latest bash
root@ad154f4ab3c4:/# apt-get update
Get:1 http://archive.ubuntu.com/ubuntu jammy InRelease [270 kB]
Get:2 http://security.ubuntu.com/ubuntu jammy-security InRelease [99.4 kB]
Err:2 http://security.ubuntu.com/ubuntu jammy-security InRelease
The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 871920D1991BC93C
Get:3 http://archive.ubuntu.com/ubuntu jammy-updates InRelease [109 kB]
Err:1 http://archive.ubuntu.com/ubuntu jammy InRelease
The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 871920D1991BC93C
Err:3 http://archive.ubuntu.com/ubuntu jammy-updates InRelease
The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 871920D1991BC93C
Get:4 http://archive.ubuntu.com/ubuntu jammy-backports InRelease [90.7 kB]
Err:4 http://archive.ubuntu.com/ubuntu jammy-backports InRelease
The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 871920D1991BC93C
Reading package lists… Done
W: http://security.ubuntu.com/ubuntu/dists/jammy-security/InRelease: The key(s) in the keyring /etc/apt/trusted.gpg.d/ubuntu-keyring-2012-cdimage.gpg are ignored as the file is not readable by user ‘_apt’ executing apt-key.
I’m sure Ubuntu will fix this pretty quickly, but until they do, your Gitlab pipe jobs will fail with a mysterious shell not found.
Just pin your dependencies.
Try updating docker itself to a more recent version.
(Updating docker to 20.10 fixed it for me.)
IIRC I also tried with a fresh install, which would be the latest version.
Maybe they fixed in the meanwhile, makes sense to update and fix :latest image.